今天這篇將三者結(jié)合一下,也不要太復(fù)雜。有交換機有vlan,有防火墻有域策略,再加個NAT地址轉(zhuǎn)換。
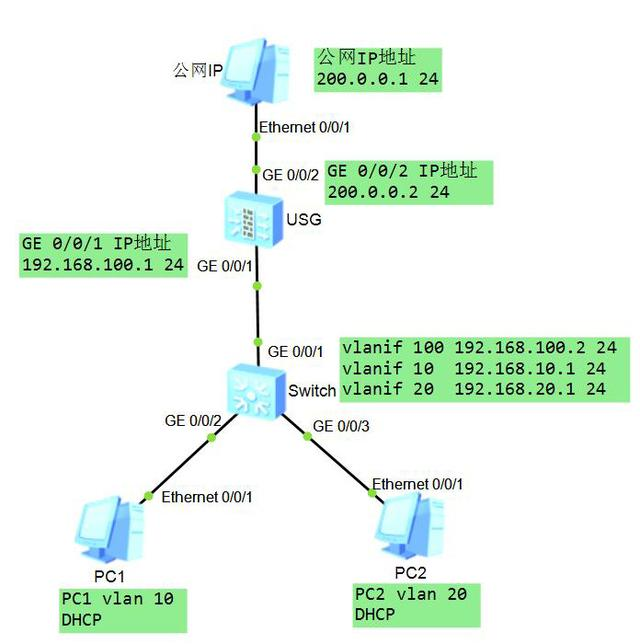
如上圖,三層交換機S5700和防火墻USG5500對接,使用戶PC1和PC2可以實現(xiàn)上網(wǎng)功能。交換機是三層交換機,可以完成跨網(wǎng)段數(shù)據(jù)轉(zhuǎn)發(fā)。
配置思路:
1、交換機作為用戶的網(wǎng)關(guān),實現(xiàn)三層轉(zhuǎn)發(fā)。同時作為DHCP服務(wù)器,為用戶分配IP地址。
2、 防火墻通過NAT轉(zhuǎn)換,使用戶可以訪問外網(wǎng)。
交換機Switch配置文件:
<Huawei>sys
Enter system view, return user view with Ctrl+Z.
[Huawei]sysname Switch
[Switch]vlan batch 10 20
[Switch]int g0/0/2 //配置PC1相連端口
[Switch-GigabitEthernet0/0/2]port link-type access
[Switch-GigabitEthernet0/0/2]port default vlan 10
[Switch-GigabitEthernet0/0/2]quit
[Switch]int gigabitethernet0/0/3 //配置PC2連接端口
[Switch-GigabitEthernet0/0/3]port link-type access
[Switch-GigabitEthernet0/0/3]port default vlan 20
[Switch-GigabitEthernet0/0/3]quit
[Switch]int vlanif 10
[Switch-Vlanif10]ip address 192.168.10.1 24 //配置PC1網(wǎng)關(guān)
[Switch-Vlanif10]quit
[Switch]int Vlanif 20
[Switch-Vlanif20]ip address 192.168.20.1 24 //配置PC2網(wǎng)關(guān)
[Switch-Vlanif20]quit
[Switch]vlan batch 100
[Switch]int g0/0/1 //配置連接防火墻的接口和對應(yīng)的VLANIF接口
[Switch-GigabitEthernet0/0/1]port link-type access
[Switch-GigabitEthernet0/0/1]port default vlan 100
[Switch-GigabitEthernet0/0/1]quit
[Switch]int vlanif 100
[Switch-Vlanif100]ip address 192.168.100.2 24
[Switch-Vlanif100]quit
[Switch]ip route-static 0.0.0.0 0.0.0.0 192.168.100.1 //配置缺省路由
[Switch]dhcp enable
[Switch]int vlanif 10
[Switch-Vlanif10]dhcp select int //使能DHCP服務(wù)
[Switch-Vlanif10]dhcp server dns-list 218.85.157.99 218.85.152.99 //自動分配的主從DNS服務(wù)器
[Switch-Vlanif10]quit
[Switch]int vlanif 20
[Switch-Vlanif20]dhcp select int
[Switch-Vlanif20]dhcp server dns-list 218.85.157.99 218.85.152.99
[Switch-Vlanif20]quit
防火墻USG配置文件:
<SRG>system-view
[SRG]sysname USG
[USG]interface g0/0/1
[USG-GigabitEthernet0/0/1]ip address 192.168.100.1 255.255.255.0 //配置連接交換機的接口對應(yīng)的IP地址
[USG-GigabitEthernet0/0/1]quit
[USG]interface g0/0/2
[USG-GigabitEthernet0/0/2]ip address 200.0.0.2 255.255.255.0 //配置連接公網(wǎng)的接口對應(yīng)的IP地址
[USG-GigabitEthernet0/0/2]quit
[USG]ip route-static 0.0.0.0 0.0.0.0 200.0.0.1 //配置缺省路由
[USG]ip route-static 192.168.0.0 255.255.0.0 192.168.100.2 //配置回城路由
[[USG]firewall zone trust //配置Trust可信任域并開啟域間策略
[USG-zone-trust]add interface g0/0/1 //將防火墻的G0/0/1口加入Trust域
[USG-zone-trust]quit
[USG]firewall zone untrust //配置非可信任Untrust域并開啟域間策略
[USG-zone-untrust]add interface g0/0/2 //將防火墻的G0/0/2口加入Untrust域
[USG-zone-untrust]quit
[USG]firewall packet-filter default permit all //開啟所有域的域空間策略
Warning:Setting the default packet filtering to permit poses security risks. You
are advised to configure the security policy based on the actual data flows. Ar
e you sure you want to continue?[Y/N]y
[USG]nat address-group 1 200.0.0.2 200.0.0.2 //配置NAT地址池
[USG]nat-policy interzone trust untrust outbound
[USG-nat-policy-interzone-trust-untrust-outbound]policy 1
[USG-nat-policy-interzone-trust-untrust-outbound-1]policy source 192.168.0.0 0.0.255.255 //NAT轉(zhuǎn)換對象是192.168.0.0網(wǎng)段的內(nèi)網(wǎng)IP地址
[USG-nat-policy-interzone-trust-untrust-outbound-1]action source-nat
[USG-nat-policy-interzone-trust-untrust-outbound-1]address-group 1
[USG-nat-policy-interzone-trust-untrust-outbound-1]quit
[USG-nat-policy-interzone-trust-untrust-outbound]quit
測試結(jié)果
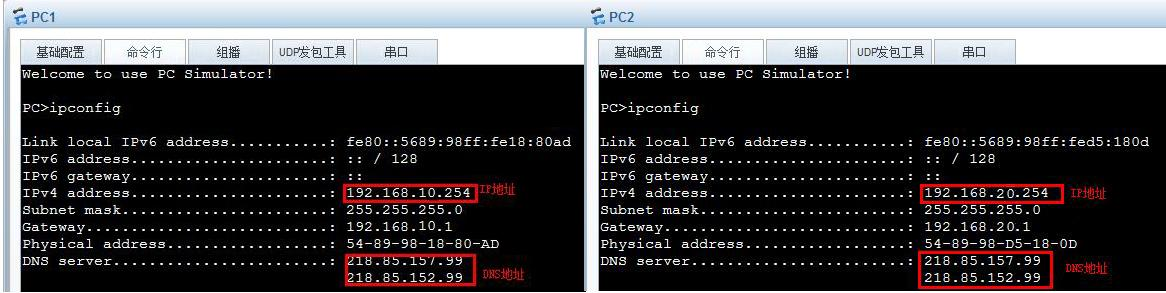
PC1與PC2成功DHCP到所在VLAN的IP和DNS地址
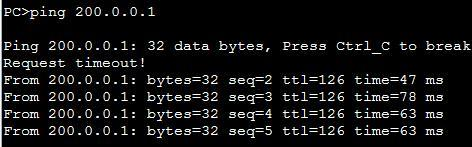
PC1PC2成功ping通公網(wǎng)PC